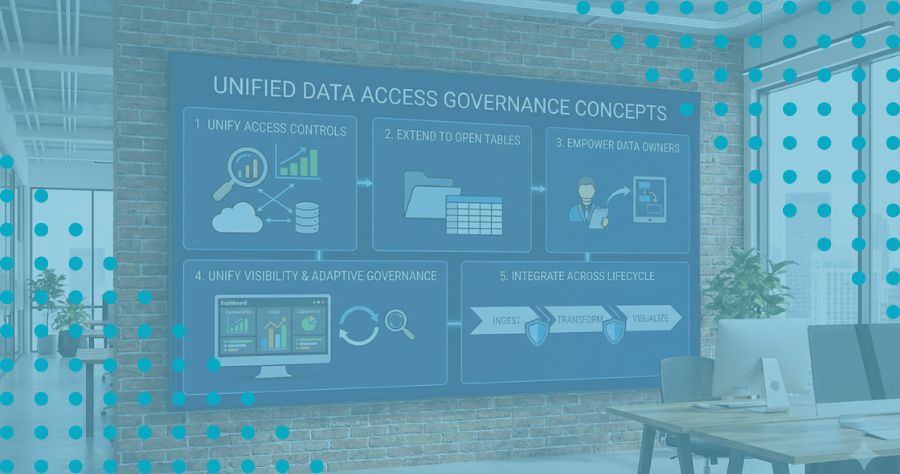
The Challenges of Securing Enterprise Data Products at Scale


Across industries, organizations are racing to build enterprise-class data products in Databricks and Snowflake—reusable, governed data assets that power analytics, AI models, and real-time business decisions. These products are transforming how data flows across the enterprise, but they’re also revealing a hard truth: as the number of data products grows, so does the complexity of keeping them secure and compliant from source to dashboard.
Scaling Enterprise Data Product Access
Databricks continues to strengthen its access governance framework with powerful features like Unity Catalog, which provides a strong foundation for visibility and control. Similarly, Snowflake continues to build out functionality in Horizon Catalog. As enterprises adopt these capabilities across hundreds of data products, however, they’re finding that access governance still requires hands-on management—writing, updating, and maintaining code to align policies with the unique structure and lifecycle of each data product.
That’s manageable with one or two products, but it quickly becomes overwhelming at scale.
Global enterprises are now managing hundreds of data products and AI agents—each with its own policies, permissions, and maintenance requirements. The access governance effort multiplies, consuming engineering time and slowing delivery.
The Security Disconnect Between Databricks, Snowflake, and Power BI
The challenge doesn’t stop at the data product.
Once a data product is ready for business users, it’s typically surfaced through Power BI or Tableau dashboards. This is where access governance often breaks down.
Access controls defined in Databricks or Snowflake don’t automatically extend into Power BI, forcing teams to rebuild permissions, filters, and row-level security for every dashboard. Multiply that across dozens of products and hundreds of reports, and the process becomes unmanageable.
Consider a real-world example: A multinational company’s finance organization relies on source data in Databricks or Snowflake to analyze mergers and acquisitions. The data team curates sensitive financial data, then shares it with business users and external advisors from firms like McKinsey or BCG. Each audience needs different access levels.
Without a seamless way to extend policies from the data source into Power BI, teams must manually replicate dashboards for every access scenario, which can add up to hundreds of times, just to maintain compliance.
The end result is fragile, manual access governance that slows down business decisions while increasing risk.
The Real Cost of Manual Security
This friction isn’t just technical; it’s organizational. Developers spend weeks coding and validating policies. Compliance and legal teams review every new connection or data source. Risk and privacy approvals can take weeks or even months, especially when sensitive or regulated data is involved.
A typical scenario underscores the imbalance: building the data product takes a week, while fixing the compliance issues takes four.
At enterprise scale, those delays translate directly into lost agility and rising operational cost at a time when most companies are under pressure to do more with fewer people.
Why the Enterprise Data Product Problem Is Growing
Data has never been this close to the business. Today, business units themselves are co-developing data products with IT—linking datasets directly to revenue, customer experience, and strategic KPIs. That shift is positive, but it also exposes more people, processes, and tools to the same access governance gaps.
Every time a new data source is added, the organization must re-evaluate privacy, risk, and compliance. Every change triggers manual updates in Databricks or Snowflake, then in Power BI. And every delay compounds the problem.
Meanwhile, enterprises are cutting costs and limiting headcount. They can’t afford to scale security by simply hiring more people or writing more code.
The Core Challenge
The challenge isn’t building data products: it’s securing them and governing data access at enterprise scale, all the way from ingestion to visualization.
Enterprises need a way to keep security and compliance continuous as data moves through every stage, without slowing down delivery.
Until that happens, the very process of scaling data products will continue to create friction, cost, and risk, even in the most advanced data platforms.
Stay in the Know
Subscribe to Our Blog