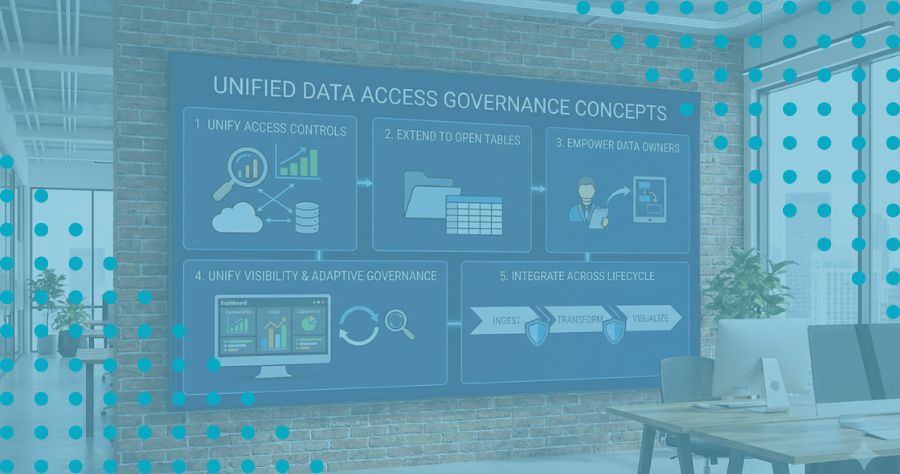
Data Domains: Local Control, Global Guardrails


Imagine a financial analyst on the finance team needs access to asset and portfolio data stored in a Snowflake table. She submits a request, but it gets routed through a central data governance team that doesn’t have context on her role or urgency. The security team flags it for review due to sensitive asset pricing fields, and days go by with back-and-forth emails, approvals, and unclear responsibilities. Eventually, she gets access—but only after a frustrating delay and with more permissions than she actually needs.
This kind of friction is common in large organizations where centralized access control struggles to keep up with the needs of distributed teams. As more business units own and use their own datasets, traditional models slow everything down—policy updates, access approvals, and, ultimately, productivity.
Data Domains, a preview feature in TrustLogix, solves this by enabling federated access control—delegating policy control to domain-specific owners while preserving centralized visibility and oversight.
What Are Data Domains?
Data Domains let organizations group data assets into logical business domains (e.g., Finance, HR, Customer Support) and assign ownership over access policies to the people who understand the data best. These domains contain one or more data products, which in turn include specific assets like databases, schemas, and tables mapped to underlying data sources such as Snowflake and Databricks.
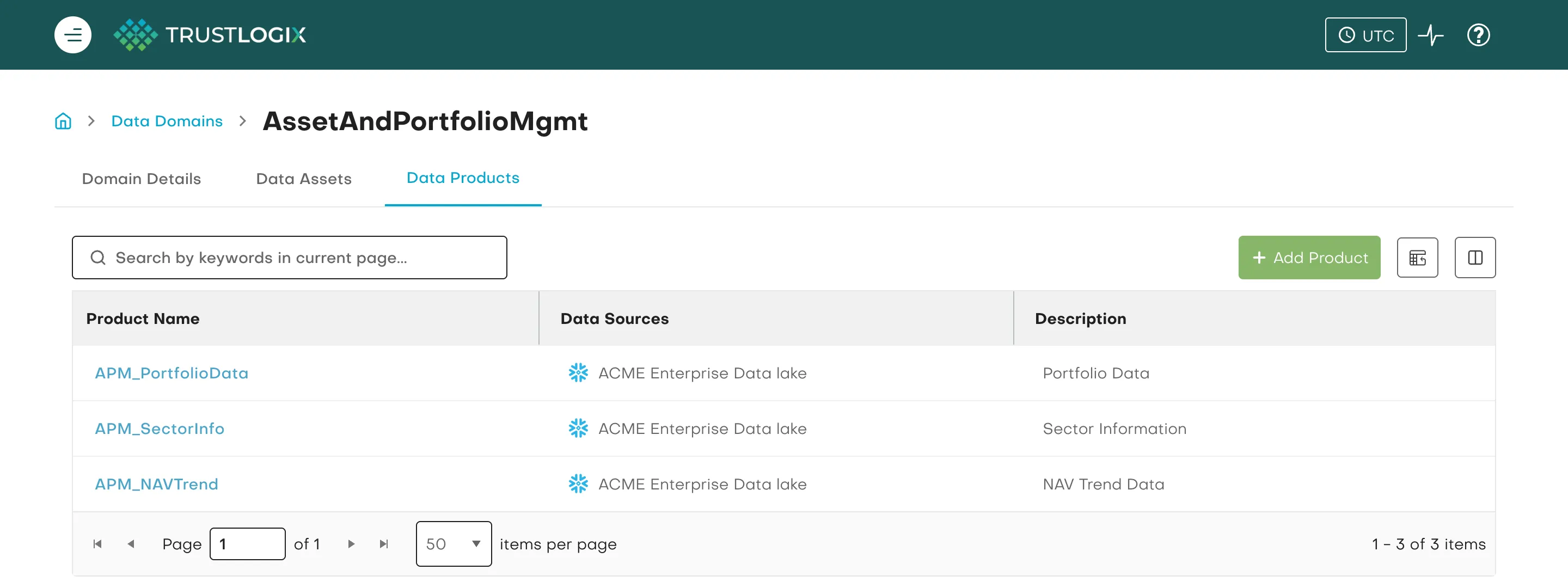
This structure allows Policy Administrators to manage access policies—such as RBAC, ABAC, and data masking—within their own domain. They can tailor controls to fit the nuances of their business area, while Super Users or Admins retain control over domain structure, cross-domain templates, and global governance standards.
Federated Access, Without Losing Control
With Data Domains, access decisions are no longer held up by a central bottleneck. Instead, ownership shifts to domain-aligned teams who can move faster because they have the context needed to make informed decisions.
At the same time, the system is designed with guardrails:
- Domain-scoped administrators can’t modify global templates or affect assets outside their domain.
- All actions are tracked, and policy enforcement is clearly scoped.
- Templates and controls can be pre-defined at the domain level to maintain policy consistency.
This balance between local agility and centralized control is key to scaling access governance without compromising on security or compliance.
Bridging the Gap Between Data Owners and Security Teams
Access decisions often sit at the intersection of business context and security policy—but in many organizations, data owners and SecOps teams operate in silos. Data owners know who needs access, while security teams know what’s safe—but without shared visibility, it’s difficult to work together effectively and efficiently.
Data Domains bring both sides onto the same page by providing scoped visibility, domain-level control, and centralized oversight. Data owners can define access aligned with business needs, while security teams ensure compliance through clear, auditable guardrails.
The result? Faster decisions, fewer conflicts, and more secure collaboration.
Built for Scale
The Data Domain feature is designed with large, complex data environments in mind. It supports:
- Clear separation of duties between global and domain administrators.
- Structured mappings of data products and assets to specific domains.
- Support for role-, attribute-, and relationship-based policy creation tailored to domain-specific contexts.
- Enforced boundaries that prevent cross-domain interference.
As your data landscape grows, this model helps ensure your governance strategy keeps up—without overloading central teams or leaving access decisions in the wrong hands.
Data Domain provides a scalable, collaborative model for access governance. By combining delegated policy control with centralized oversight, TrustLogix helps organizations reduce friction, improve compliance, and align business and security teams around shared data stewardship.
To preview this feature, please schedule a demo.
Stay in the Know
Subscribe to Our Blog