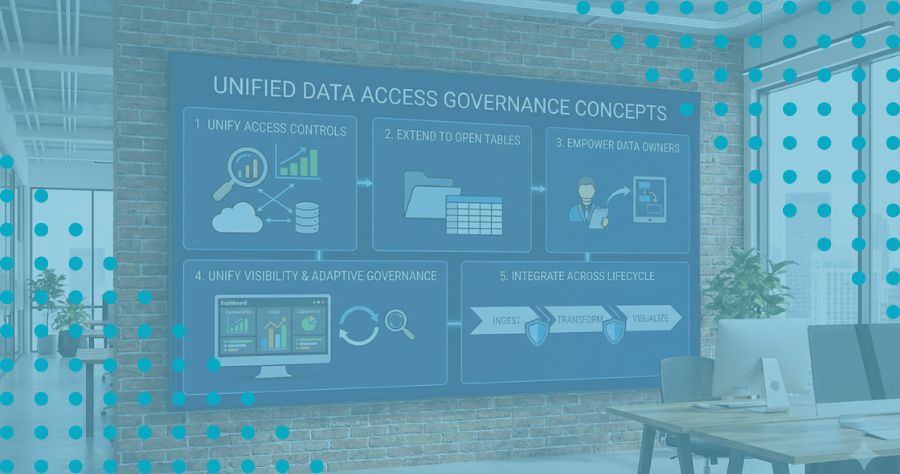
Data Access Governance: The Importance of a Definitive Source For Access Controls


As enterprises adopt modern data platforms like Snowflake and Databricks across AWS, Azure, and GCP, securing sensitive data becomes exponentially more complex. Teams struggle to maintain consistent access controls as policies fragment across clouds, warehouses, and analytics tools. TrustLogix solves this by providing a centralized, policy-driven control plane—giving organizations a unified approach to managing access, visibility, and compliance across their entire data ecosystem.
The Data Access Governance Challenge
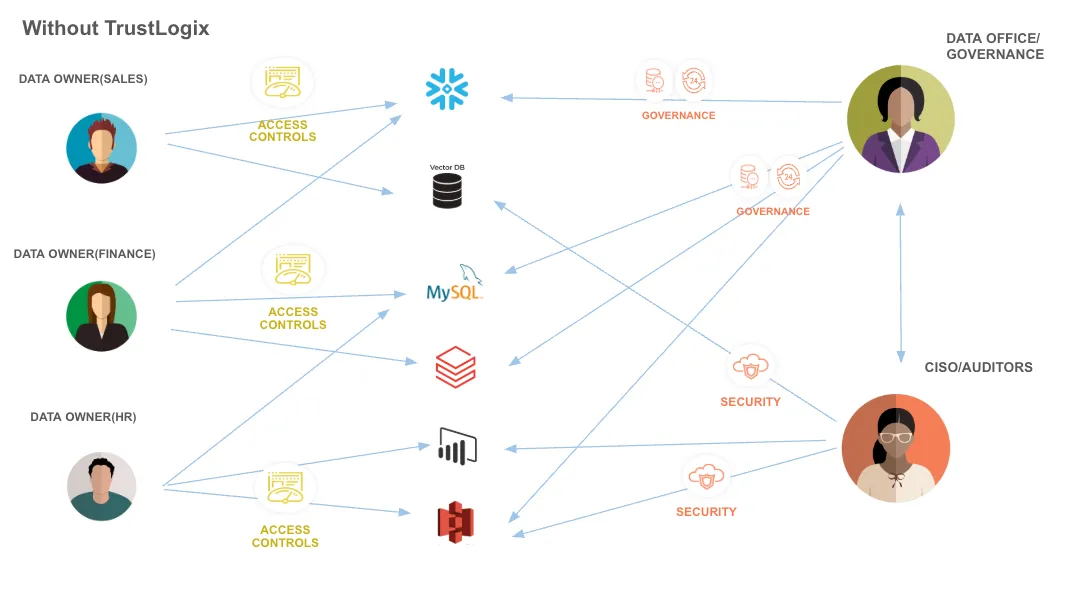
Modern enterprises utilize various data platforms, from cloud data warehouses like Snowflake and Databricks to data lakes on AWS and Azure and relational databases like SQL Server, PostgreSQL, and MySQL. This diversity leads to several key issues.
- Inconsistent Policy Implementation: Policies configured independently across platforms often lead to inconsistencies and security gaps.
- Lack of Visibility: Security teams struggle to maintain a comprehensive view of who has access to what data across the organization.
- Audit Complexities: Demonstrating compliance becomes a manual, error-prone process requiring evidence collection from multiple systems.
- Policy Drift: Platform-specific modifications create discrepancies between intended and actual access controls over time.
Why a Definitive Source for Data Access Governance Controls Matters
A unified source for access controls streamlines policy definition, deployment, and monitoring:
Unified Policy Definition: Organizations can centrally define data access control policies using business-friendly language. This approach enables consistent policy application that is aligned with business needs.
Automated Deployment: Centralized policies into platform-specific implementations, simplifying deployment across different environments using CI/CD pipeline while minimizing human error.
Enhanced Data Access Governance: A unified source of truth establishes clear ownership and access controls, ensuring data integrity and facilitating efficient auditing and compliance.
Continuous Monitoring: Real-time policy deviation detection helps identify unauthorized grants, missing implementations, and privilege escalations, ensuring compliance.

Implementing One Source For Data Access Governance Controls
- Focus on Critical Data: Start with the most sensitive or regulated data assets.
- Establish Ownership: Define which teams manage policy creation versus technical implementation.
- Plan Integration: Identify connectivity to relevant data platforms and identity providers.
- Standardize Policies: Use consistent naming and structure for access policies. Develop templates for typical access patterns
- Develop a Monitoring Strategy: Set alert thresholds and response procedures for policy deviations.
- Align with CI/CD: Integrate policy workflows with existing CI/CD practices and tools.
Final Thought
As data ecosystems grow complex, managing access controls separately becomes unsustainable. Platforms like TrustLogix provide a definitive source for access controls, strengthening security, simplifying compliance, and enabling better data utilization. Integrating with CI/CD pipelines enhances automation, consistency, and scalability. Continuous monitoring enables privacy by design to ensure security standards are upheld despite ongoing changes in the modern data environment.
We'd love to hear your thoughts and experiences regarding data access governance. Drop us a line at hello@trustlogix.io and share what your thinking.
Stay in the Know
Subscribe to Our Blog