Snowflake Summit 2025: Security and Governance Highlights


A key message from Snowflake Summit 2025 was simplification—making it easier for organizations to build with data, deploy AI, and enforce governance at scale. As more enterprises look to unlock value from AI across the full data lifecycle, Snowflake is reimagining how data engineering, analytics, application development, and collaboration work together on a unified, secure platform.
New capabilities like Snowflake Intelligence, Cortex AISQL, and the Data Science Agent simplify AI adoption by removing infrastructure complexity and enabling users to interact with data using natural language—while keeping sensitive information protected. Meanwhile, enhancements to Horizon Catalog, Trust Center, and Copilot focus on streamlining governance and security, helping organizations scale responsibly without losing control.
Data Governance and Security in Snowflake
At Snowflake Summit, Snowflake announced significant updates to Horizon Catalog, which now supports external data discovery across relational databases, dashboards, semantic models, and Iceberg tables. A new Copilot for Horizon Catalog introduces natural language capabilities for metadata and policy management, making governance tasks faster and more accessible.
Trust Center enhancements include AI-driven anomaly detection, real-time monitoring, and continuous risk posture assessment—enabling organizations to proactively detect suspicious activity, misconfigurations, and access issues. Additional features like leaked password protection, bad IP blocking, and expanded sensitive data reporting provide built-in safeguards, while new authentication options—such as passkey-based MFA, workload identity federation, and programmatic access tokens—modernize access control and help ensure data protection is both continuous and scalable.
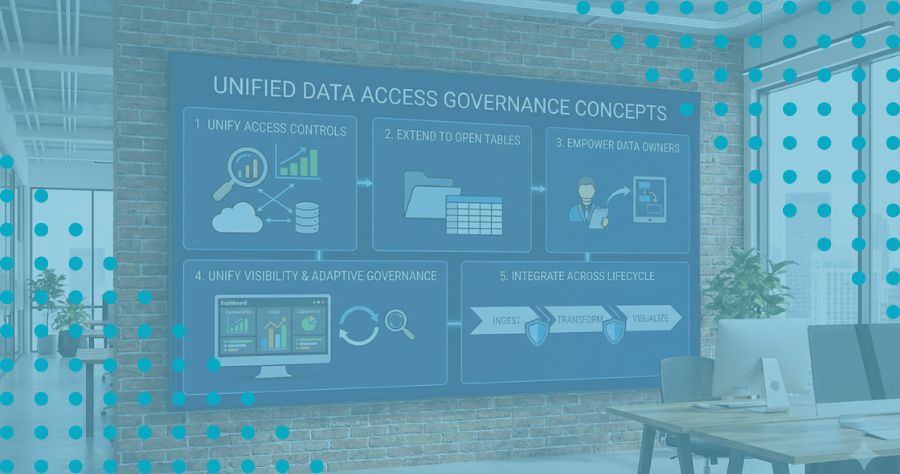
Shifting Toward Centralized, Policy-Based Access
A recurring theme throughout Snowflake Summit was the shift toward centralized, policy-based access control. Instead of managing permissions separately in each tool, organizations are defining policies based on business attributes—like department or region—and applying them consistently across platforms. This reflects a broader move toward scalable, automated data governance as enterprises navigate complex environments and evolving regulations.
One Snowflake customer shared their journey in building a comprehensive governance foundation that empowers data teams with the access they need while maintaining centralized oversight. By replacing fragmented, manual processes with unified policy enforcement, automated provisioning, and least-privilege controls, organizations are not only improving compliance and reducing overhead—they’re also delivering faster, more secure access to data that ultimately enhances the customer experience.
Another example is when sensitive data moves downstream from platforms like Snowflake into tools like Microsoft Power BI, where access controls often don’t carry over automatically. Without a unified approach, teams are left maintaining redundant policies manually, an approach that doesn't scale and puts sensitive data at risk. During the summit, TrustLogix showed how to automate this process by extending source-defined policies into Power BI, applying real-time filtering and masking, and continuously monitoring for policy violations—ensuring consistent governance throughout the analytics stack.
Securing Data for AI Agents
Another emerging concern was how to secure AI agents that interact with systems like AI agents interacting with systems like Salesforce or cloud data warehouses often lack the context to enforce access rules, creating governance blind spots. To mitigate this, organizations are emphasizing clear data ownership, reliable metadata, and governed data marketplaces as essential foundations for secure, explainable, and effective AI.
TrustLogix demonstrated a solution for securing the data used by AI agents by enforcing access policies at the data layer. When an agent submits a query, TrustLogix intercepts the request, evaluates it based on the user’s entitlements, and rewrites or filters the query accordingly—masking sensitive fields or blocking unauthorized data as needed. This ensures that AI agents can operate efficiently without bypassing established security and compliance boundaries.
Supporting Innovation and Compliance
The conversations at Snowflake Summit made it clear that organizations are actively rethinking how they govern access, enforce policies, and scale data security in a way that supports both innovation and compliance. As the tools evolve, so too must the strategy. Centralized policy management, real-time enforcement, and automation are no longer nice-to-haves—they’ve become essential.
Stay in the Know
Subscribe to Our Blog